Is Facebook Keeping Your Password Secure?
The answer is yes if keeping passwords in plain text is considered secure. The obvious answer is NO. No, Facebook has failed you once again.… Read More »Is Facebook Keeping Your Password Secure?

The answer is yes if keeping passwords in plain text is considered secure. The obvious answer is NO. No, Facebook has failed you once again.… Read More »Is Facebook Keeping Your Password Secure?
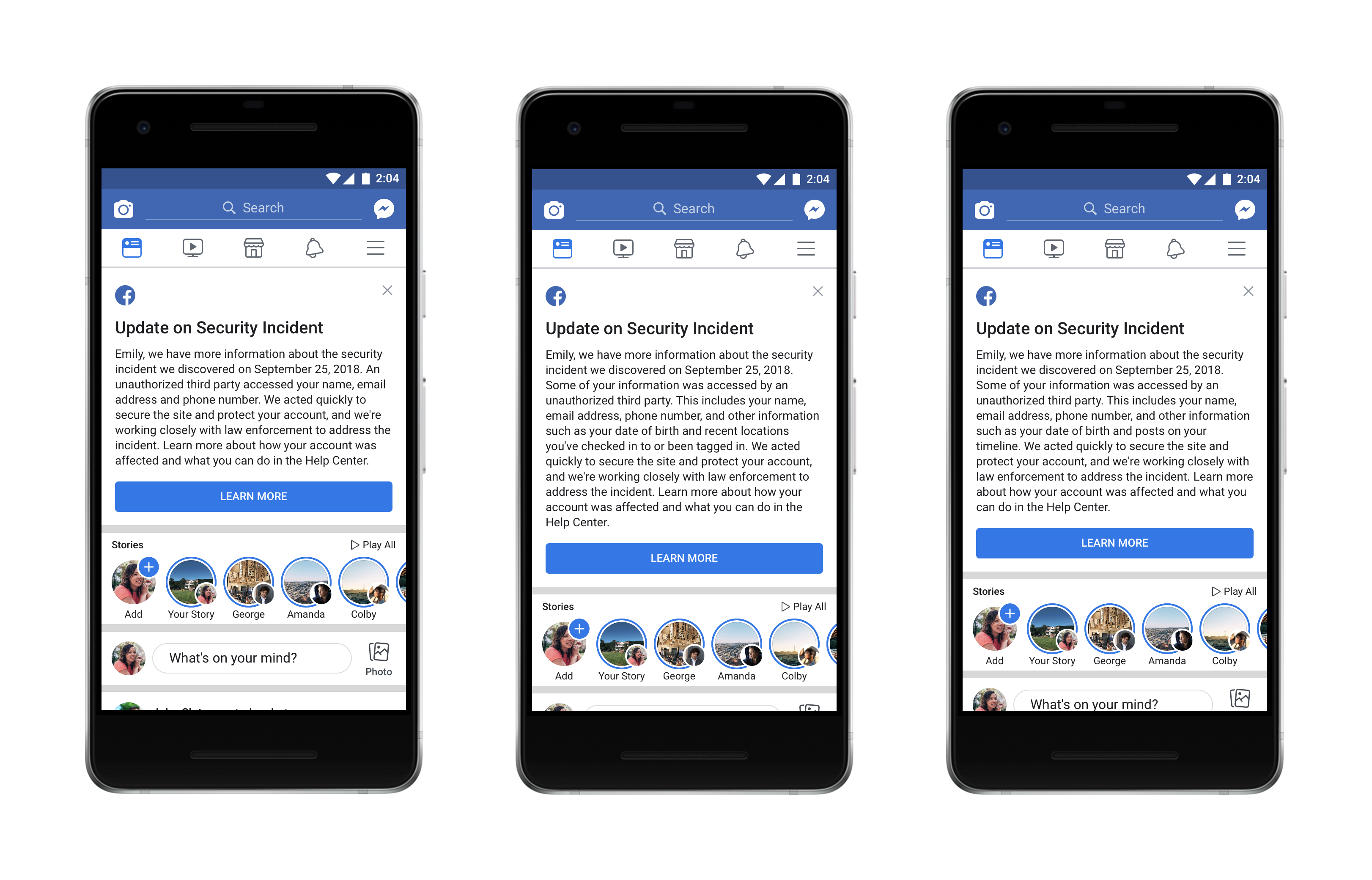
Facebook published this October 12, 2018 an update on the attack that we presented to you just about two weeks ago in an article titled Facebook… Read More »Update On The Facebook Hack – Are You One Of The 30 Million Users Who Got Hacked?
Facebook just published a Security Update about a major Security Breach that exploited the View As feature and other code modifications done to Facebook in… Read More »Facebook Hack – Over 90 Million Accounts Affected. Is Your Facebook Account Affected?
In one more of these wonderful scripts that can do crazy things, philastokes from APPLEWRITERHELPER, has handed you the keys to the kingdom. With this… Read More »When Was The Password Last Changed On This Mac?
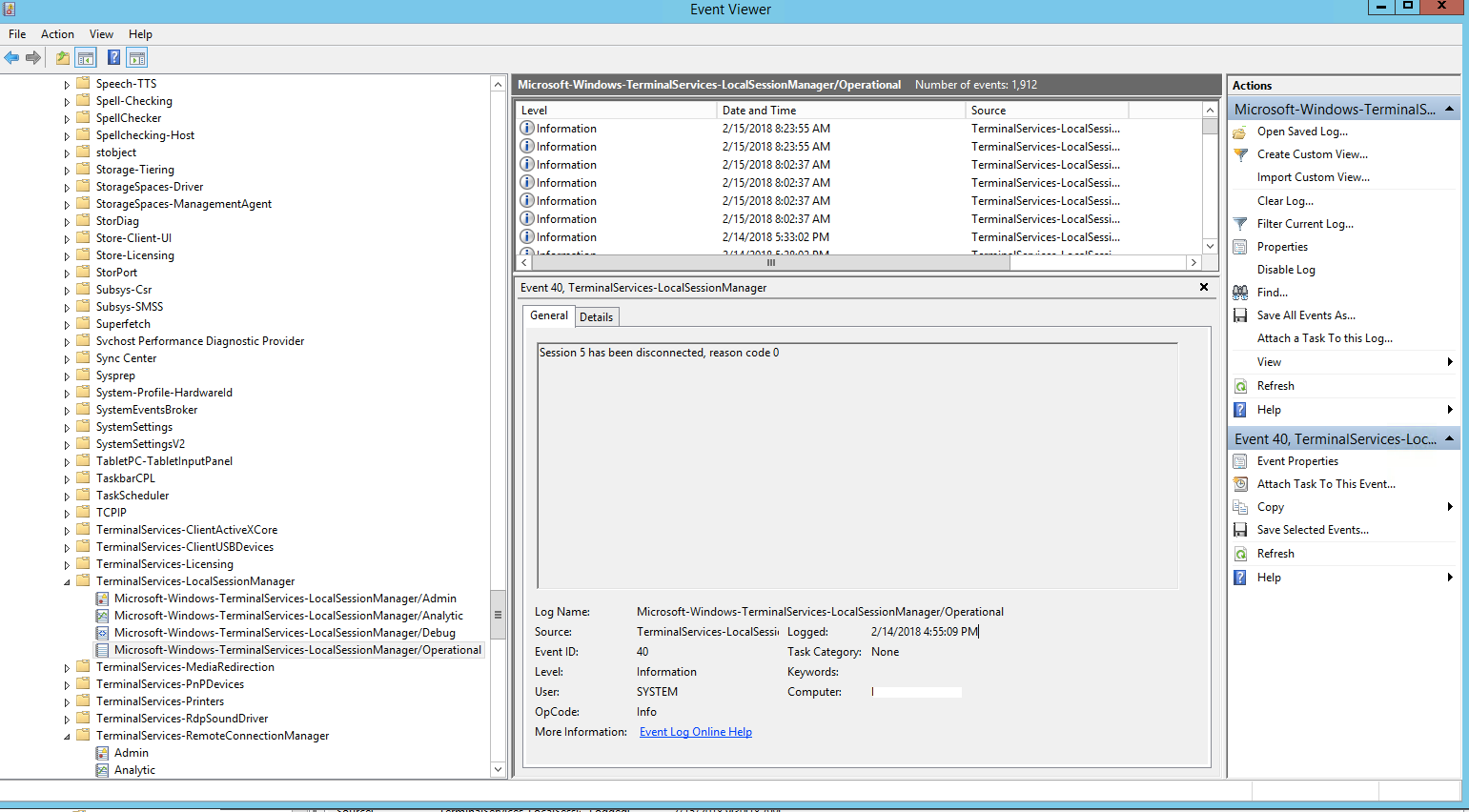
The first time I used these logs is when I was running an audit to figure out whether a specific user has recently accessed my… Read More »How To Find Out All Remote Desktop Logon Sessions That Took Place On Windows Server 2012 R2

Hello, Friends, Uber has suffered a data breach a year ago, and the address and email information of 57 million people were stolen. Uber paid… Read More »Security Warning – Beware of Emails About Uber