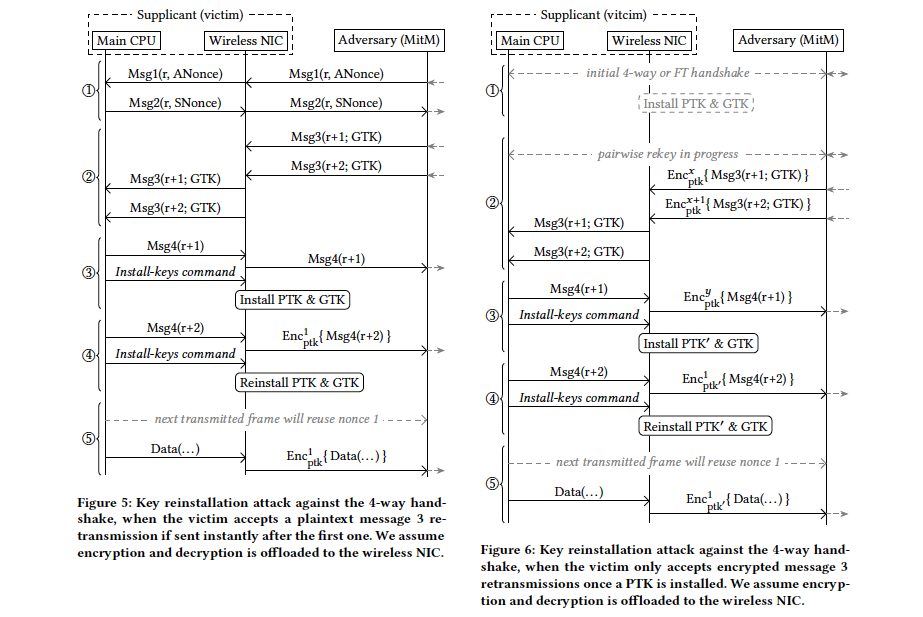
Warning – Major WannaCry-like Windows Security Exploit
If you have a Windows computer different from Windows 10 and Windows 8, you need this update! Windows 7, Windows XP, Windows Server 2003, Windows… Read More »Warning – Major WannaCry-like Windows Security Exploit