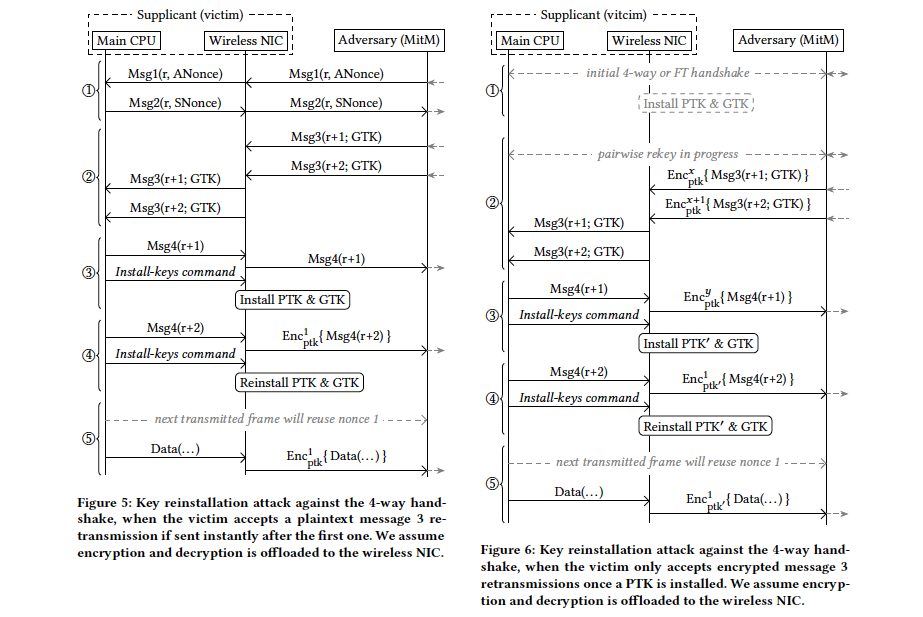
EXACTIS Database Laked – Likely Most Comprehensive Data Breach Announced
Word just go out that the marketing firm EXACTIS has in its possession a database with close to 340 million individual records available until recently… Read More »EXACTIS Database Laked – Likely Most Comprehensive Data Breach Announced