Your Debit Card Is Locked Scam
Did you get a text message stating that your Debit Card was locked? Well, do not fall for it. I may look many different ways… Read More »Your Debit Card Is Locked Scam
Did you get a text message stating that your Debit Card was locked? Well, do not fall for it. I may look many different ways… Read More »Your Debit Card Is Locked Scam
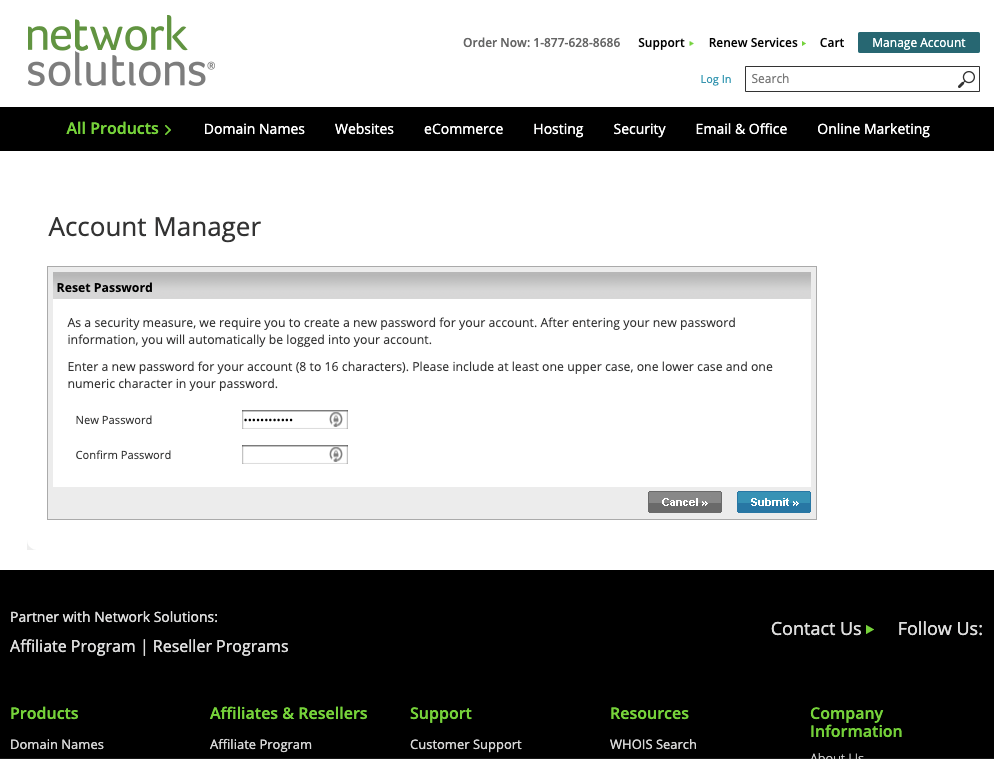
As painful as it is to announce this, what some consider the 5th largest domain registration company in the world has been breached. Or should… Read More »Cybersecurity Incident or Full Blown Breach at Web.com, Register.com, and NetworkSolutions.com

If you have ever had to manage a UniFi Video NVR from Ubiquiti, you will know what a pain it can be to try to… Read More »UniFi Video Won’t Allow Login to NVR After Firmware Upgrade
If you have a Windows computer different from Windows 10 and Windows 8, you need this update! Windows 7, Windows XP, Windows Server 2003, Windows… Read More »Warning – Major WannaCry-like Windows Security Exploit
The answer is yes if keeping passwords in plain text is considered secure. The obvious answer is NO. No, Facebook has failed you once again.… Read More »Is Facebook Keeping Your Password Secure?
According to a report this morning from SonicWall, a vulnerability that could allow remote code execution has been discovered in WinRAR. This software vulnerability exposes… Read More »Critical Vulnerability in WinRAR Exposed – Absolute Path Traversal
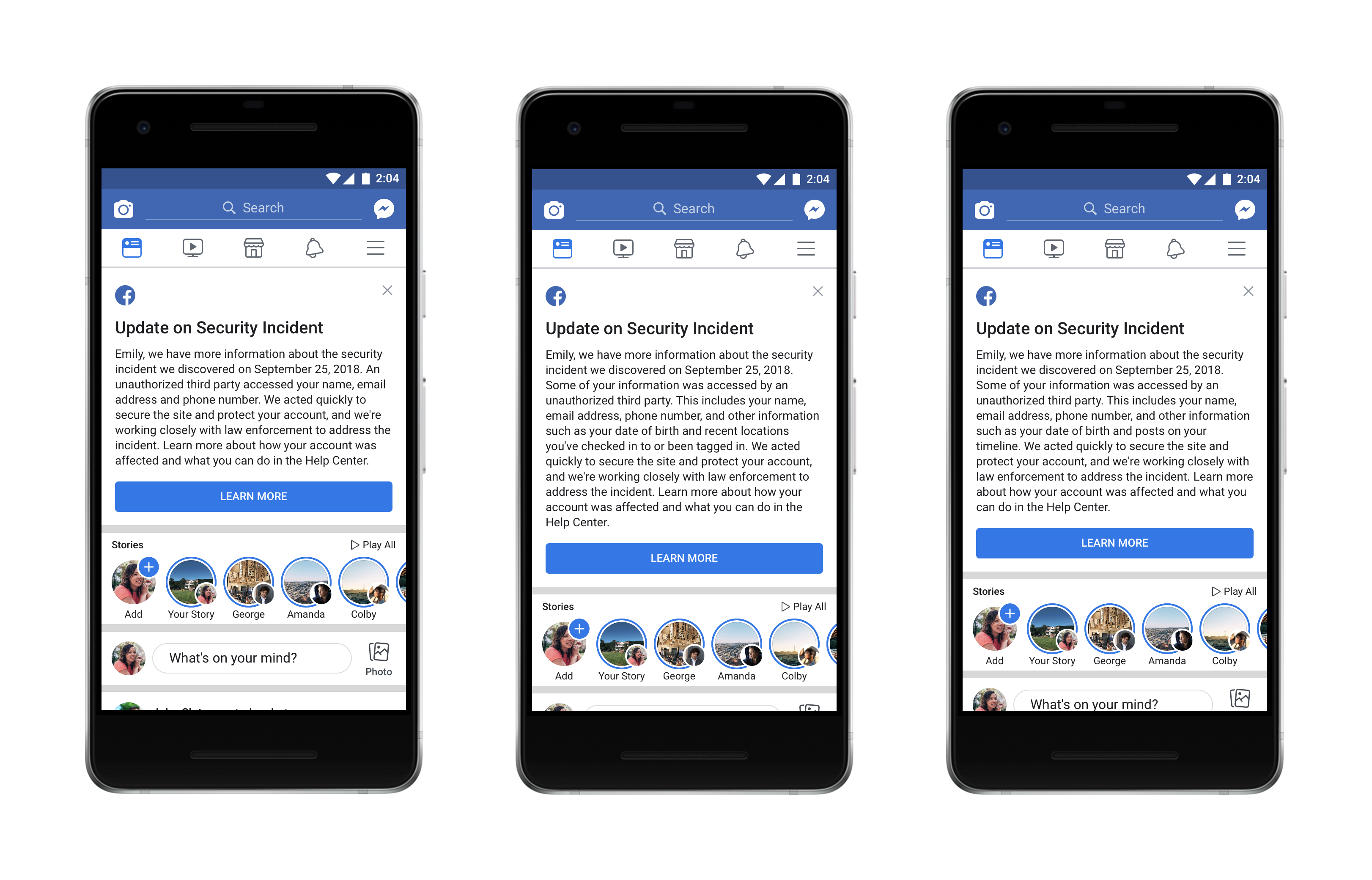
Facebook published this October 12, 2018 an update on the attack that we presented to you just about two weeks ago in an article titled Facebook… Read More »Update On The Facebook Hack – Are You One Of The 30 Million Users Who Got Hacked?
Facebook just published a Security Update about a major Security Breach that exploited the View As feature and other code modifications done to Facebook in… Read More »Facebook Hack – Over 90 Million Accounts Affected. Is Your Facebook Account Affected?
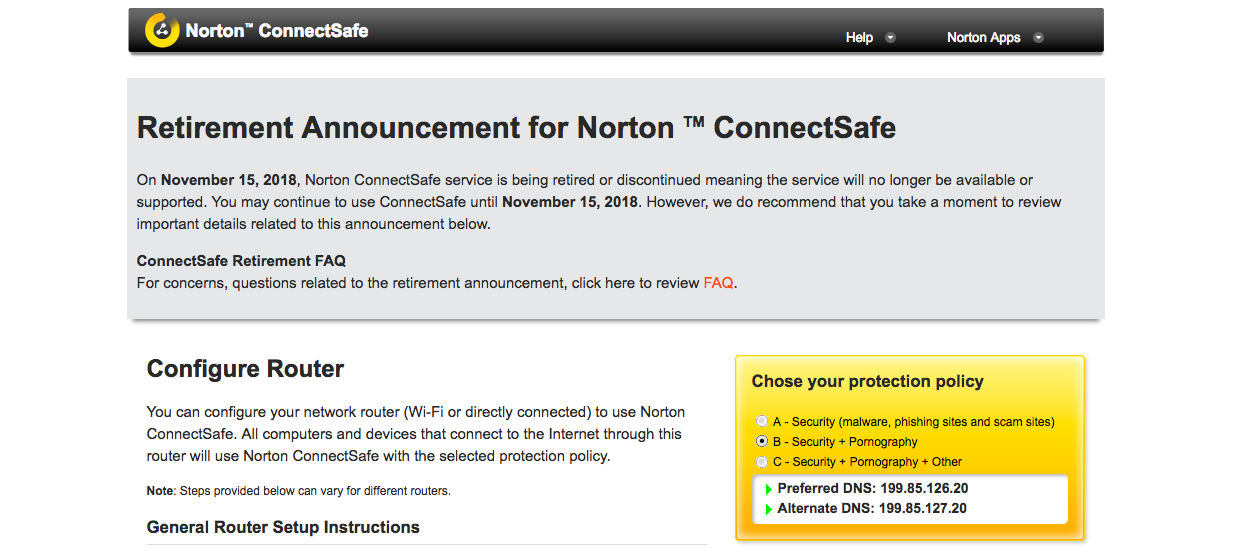
Hello, World! Your Internet connection may be going down this November 15, 2018 onward if your devices are connected to the internet via Norton ConnectSafe’s… Read More »Your Internet May Be Going Down Because Norton ConnectSafe Is Retiring
Have you ever heard of the term “idiot box?” Maybe they are not that dumb? Smart TV’s are able to watch you watch TV and… Read More »And That Is How Your TV Is Watching You