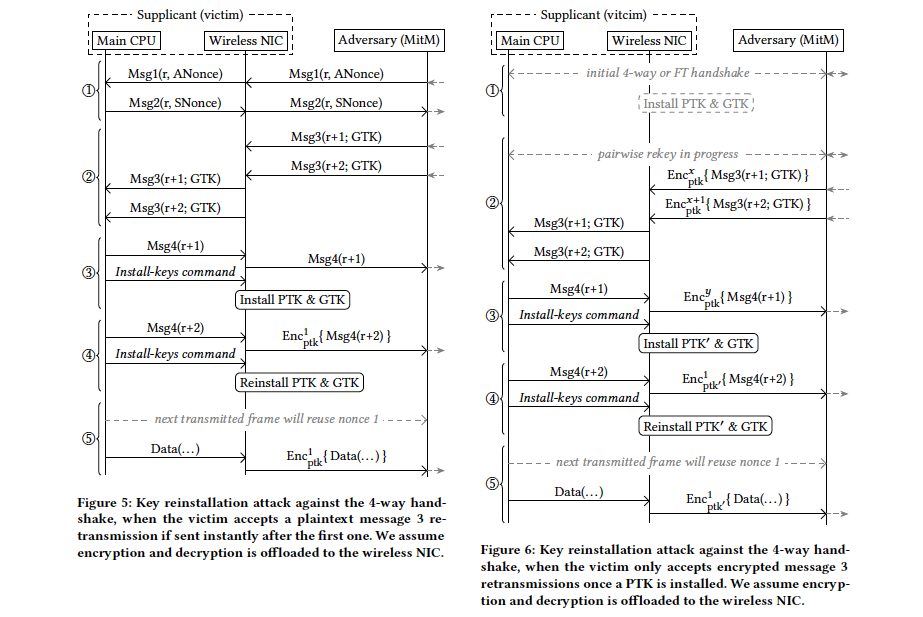
Your Internet May Be Going Down Because Norton ConnectSafe Is Retiring
Hello, World! Your Internet connection may be going down this November 15, 2018 onward if your devices are connected to the internet via Norton ConnectSafe’s… Read More »Your Internet May Be Going Down Because Norton ConnectSafe Is Retiring