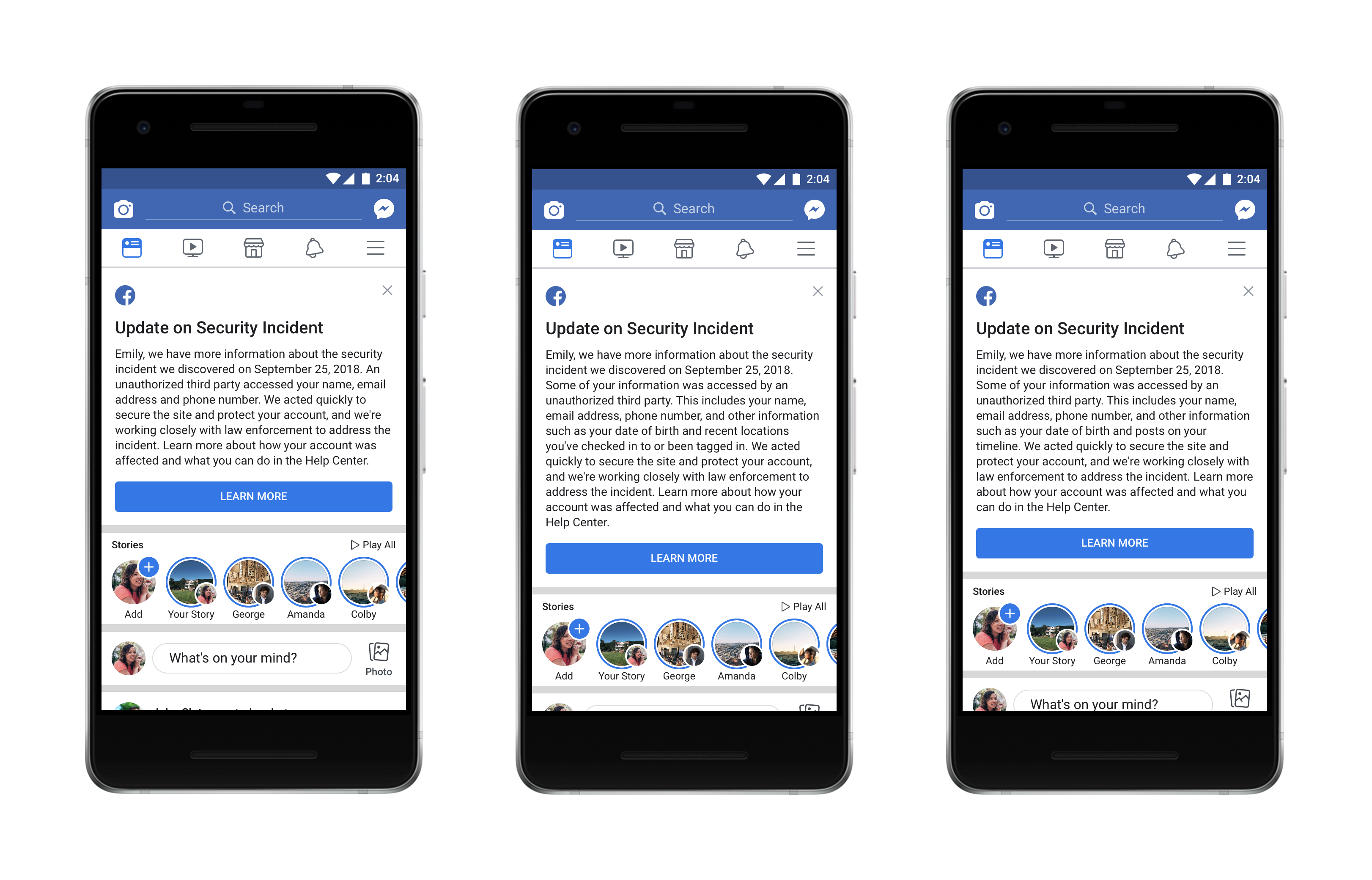
Update On The Facebook Hack – Are You One Of The 30 Million Users Who Got Hacked?
Facebook published this October 12, 2018 an update on the attack that we presented to you just about two weeks ago in an article titled Facebook… Read More »Update On The Facebook Hack – Are You One Of The 30 Million Users Who Got Hacked?