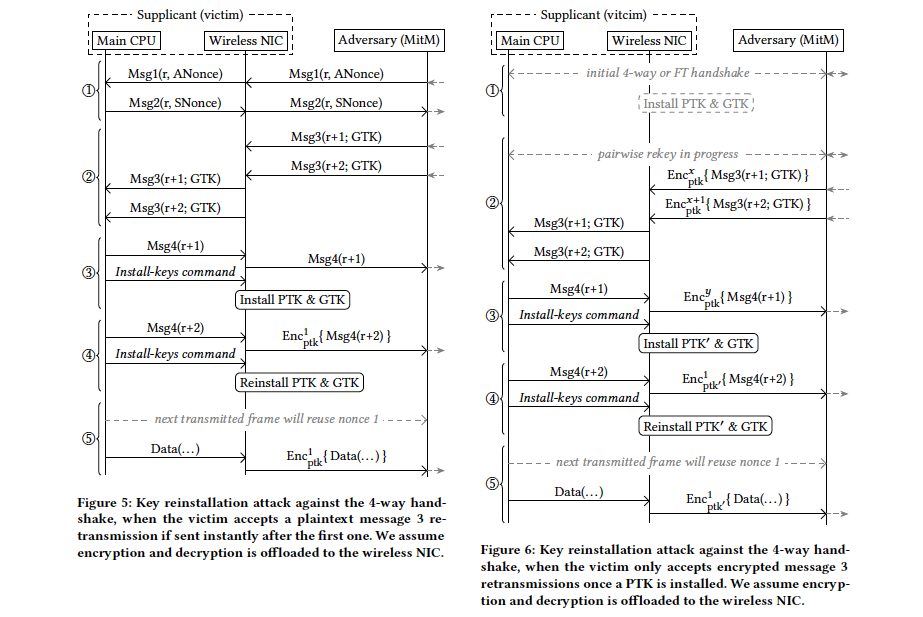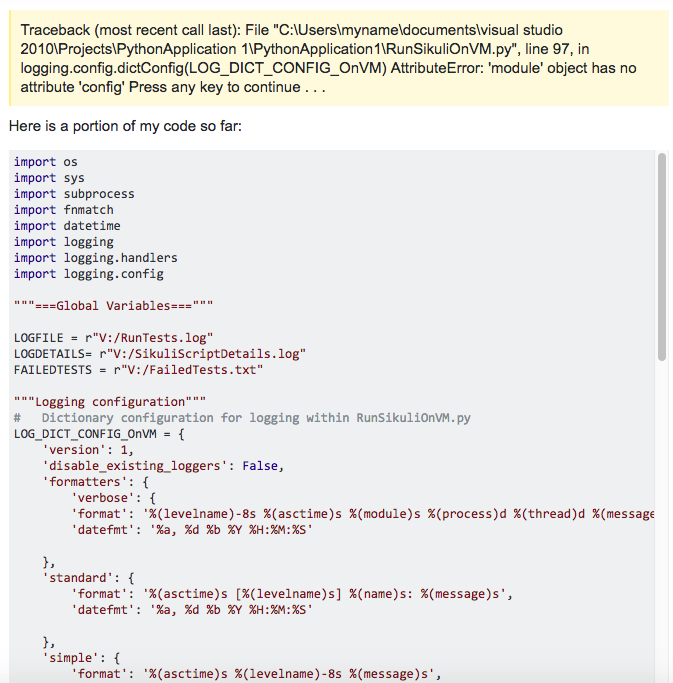
Python, AttributeError: ‘module’ object has no attribute ‘config’
“AttributeError: module object has no attribute config” is a highly common exception raised by Python. The module object in question in my case was that the logging module, which I know for sure has a config attribute.